Understand your cyber risk. Strengthen your security.
Opertiva delivers expert GRC, cloud, endpoint, and AI security assessments—plus hands-on consulting to close the gaps
How we help
Assessment
Reveal your true posture. We look beyond tool checklists to review your security maturity against modern frameworks.
-
Full Estate Review (Cloud, AI, GRC)
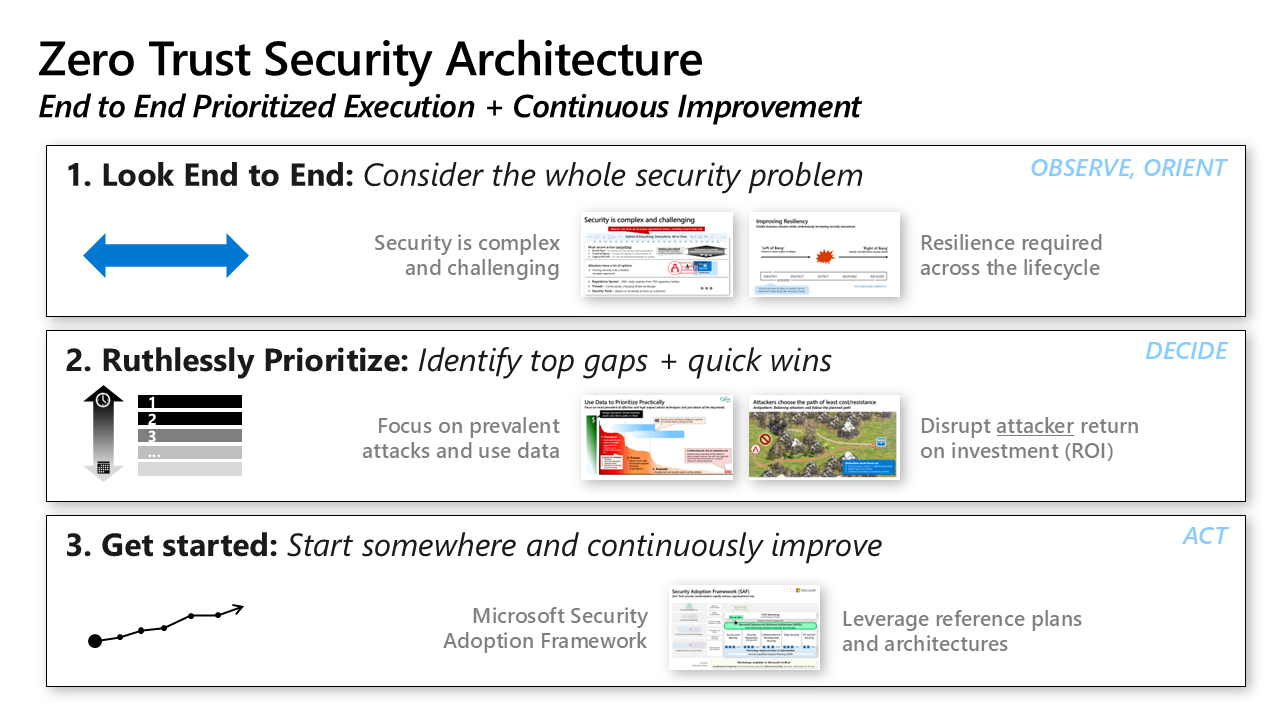
Zero Trust Architecture analysis
"Left of Bang" prevention check
OT-security assessment
Experienced in ISO27001, SIO42001, NIST CSF, Microsoft Cybersecurity Reference Architecture, CIS, NIS2, DORA, CRA.
-
You get a North Star view of your security posture, moving you from reactive firefighting to intentional governance.
Prioritization
Not everything matters equally. We help you identify what truly reduces risk and supports the business, balancing security improvements with time, cost, and operational reality.
-
Ruthless prioritization of findings
Identification of "Quick Wins"
ROI-focused roadmapping
-
Identify and address the high impact, low effort projects and initiatives
Maximize your existing investments, including Microsoft E5 or Business Premium investments - remove redundant tools
Strengthen
We support you hands-on from strategy and architecture to practical implementation. The focus is on sustainable improvements, not one-off initiatives.
-
Project implementation
Project management
Engineering & Configuration
Governance & Policy setup
Continuous improvement loops
-
Shift security from an organizational police to an enabler
Inject Opertiva consultants to your organization to quickly achieve objectives
Who we work with
We typically work with organizations that:
Operate in complex IT and cloud environments
Are growing and becoming more regulated
Want to improve security without slowing the business
Use Microsoft platforms as a core part of their environment
Wants to simplify their IT-security environment and understand if they can cut costs
Public organizations looking to get started with AI and wants good information security before deployment
Common situations we help with:
“We don’t have a clear picture of our biggest security risks”
“Security efforts feel fragmented and reactive”
“Regulatory pressure is increasing”
“We’re adopting AI but lack proper governance and controls”
“How do we know what data to secure and how do we secure it?”
“Log storage costs are to costly with our existing SIEM, optimize our log storage strategy and help us gain the observability we need”
Services
Microsoft 365 & Information Security
Microsoft 365 is increasingly shaped by AI - introducing new identities, new access paths, and new security considerations.
We help you secure Microsoft 365 with a clear focus on identity, access, and AI agent governance, ensuring that both users and AI-driven capabilities operate within defined boundaries. The result is a collaboration platform where productivity, automation, and security evolve together - without loss of control.
Common projects are:
Data discovery and classification strategy
Sensitivity labels and encryption design
Shadow AI assessments and remediations
Copilot and AI readiness projects
Monitoring of AI-assisted activities
Security
Modern environments require a modern security approach.
We help you understand your real security risks, prioritize what matters most, and integrate security across Azure and Microsoft 365. The focus is on clear governance, practical controls, and continuous improvement - not one-off fixes or unnecessary complexity. We also have specialized OT-security competence with experience in auditing and implementing robust cybersecurity in factories and advanced logistics centers.
Common projects are:
Enable and tune Defender for Endpoint, Identity, Office 365, and Cloud Apps
EDR and XDR migrations to Defender XDR
Splunk to Sentinel migrations
Log source prioritization and cost-aware configuration
SOC process and operating model
Azure
Azure is more than a cloud platform -it’s the foundation for how your IT environment can become more secure, resilient, and future-ready.
We help you assess, design, and strengthen Azure environments with a focus on governance, security, and long-term scalability, so the platform supports the business rather than constraining it.
Common projects are:
Identity and access reviews
Privileged Identity Management (PIM) design and rollout
Conditional Access and MFA strategy
Vulnerability and exposure management
Mapping Azure controls to ISO 27001, NIS2, or internal policies
Who we are
Based in Stockholm, Sweden but operate in all of the Nordics. Led by former IT management consultants and Microsoft security architects and CISSP-certified experts, we understand the ecosystem from the inside out. We ensure you apply these tools effectively to maximize the value of the investments you’ve already made.